Recent Trends in Ransomware
by Chad Siegrist, Assistant Vice President, Supervision and Regulation, and Cybersecurity Analytic Support Team, Federal Reserve Bank of Cleveland, and Jason Tarnowski, Vice President, Supervision and Regulation, and Cybersecurity Analytic Support Team, Federal Reserve Bank of Cleveland
Ransomware attacks target all industries and frequently result in direct and indirect financial losses, operational disruptions, and customer reputation consequences. In May 2021, ransomware groups attacked at least three U.S. community banks.1 However, the most notorious ransomware event in May 2021 was launched by the DarkSide (aka BlackMatter) ransomware group, which attacked Colonial Pipeline, a large oil and gas pipeline that serves the southeastern United States. The attack impacted the company’s billing system, but the firm shut down the pipeline until it could determine that the attackers hadn’t damaged or gained access to critical safety and control systems. The attack resulted in weeklong fuel shortages for large areas in the eastern and southeastern United States. Colonial Pipeline quickly paid the attackers nearly $5 million in bitcoins, but it still took several days for Colonial’s systems to be restored. While Colonial Pipeline’s incident captivated the media about the risk ransomware attacks pose to critical energy infrastructure, the financial sector is also at serious risk.
Although it is difficult to measure the total impact and financial losses resulting from ransomware attacks, the U.S. Department of the Treasury reports the dollar amount of global suspected ransomware payments between January and June 2021 exceeded that during all of 2020.2 Specific to the banking industry, one security firm reported a 1,318 percent increase in ransomware attacks targeting the financial sector during the first half of the year.3
Ransomware Impact on Community Banks
Since May 2021, at least seven community banks in California, Florida, Illinois, Kansas, Michigan, and Minnesota have become the targets of ransomware attacks, according to dark web blogs belonging to ransomware groups. Typically, these groups do not release information about affected organizations for several days to allow for initial negotiations, which suggests that the total number of community banks affected is likely far higher.
In August 2021, the AvosLocker ransomware group attacked a California community bank. In addition to encrypting and locking the bank’s computer systems, the attackers stole sensitive customer information, including names, addresses, Social Security numbers, tax forms, and loan documents. The bank notified its customers of the breach and offered credit monitoring services for the impacted customers, adding to the financial, operational, and reputational costs of the attack.4
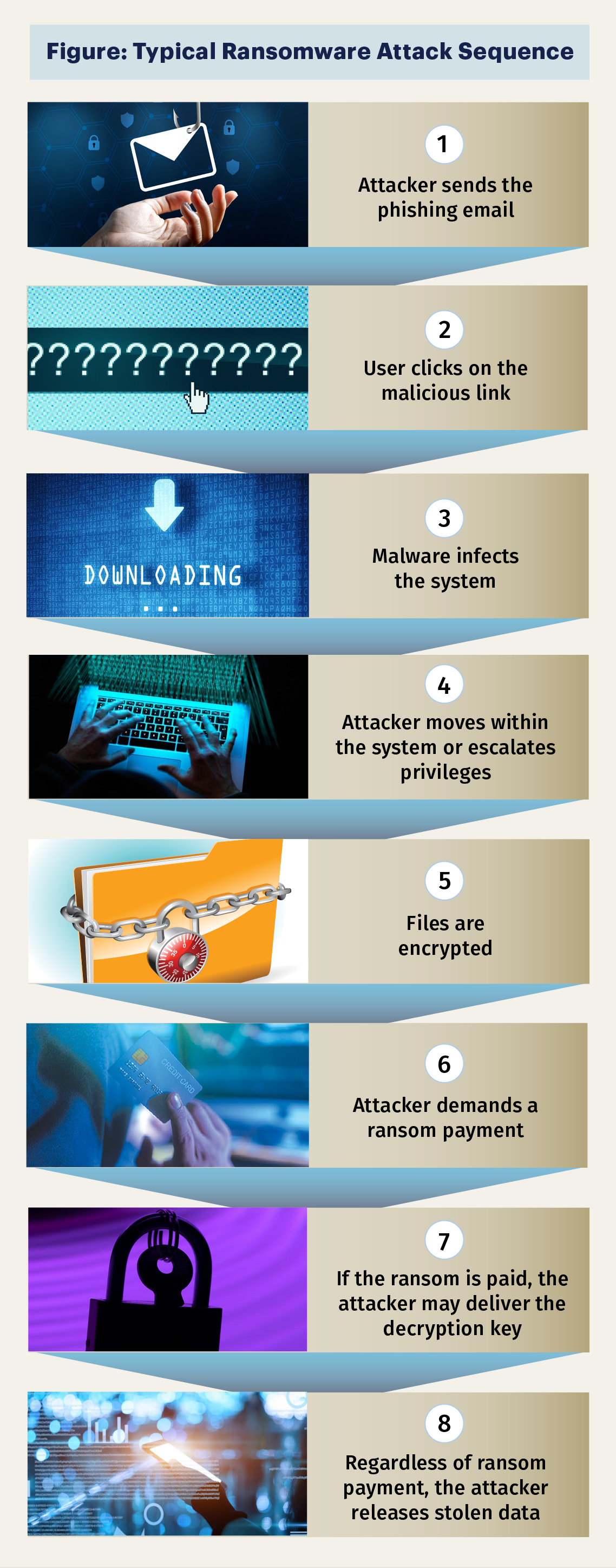
Typical Ransomware Attack Cycle
While ransomware attacks can use different tools, methods, and timing to compromise systems, there are common steps involved, as depicted in the Figure. These steps can occur over several months or in just a few minutes. Knowing how to detect and respond to each step is critical in planning response procedures and implementing effective controls, especially before the data encryption step.
Evolving Ransomware Tactics
Ransomware attackers continue to increase the sophistication of their operations. For example, ransomware groups sometimes outsource initial access and persistence steps to other “initial access brokers.” Initial access brokers specialize in gaining access to targeted organizations’ networks that the ransomware attackers then use to start the reconnaissance and encryption steps of the ransomware attack. Some ransomware groups have even established dedicated “customer support” centers to communicate with their victims, negotiate a ransom price, and explain the details of making cryptocurrency-based ransom payments.5
Ransomware attackers are also increasing their use of “double extortion attacks,” in which attackers threaten to leak stolen data if victims fail to pay the ransom. This tactic allows attackers to pressure victims to pay a ransom even if the affected organization can restore its systems from unaffected backups.
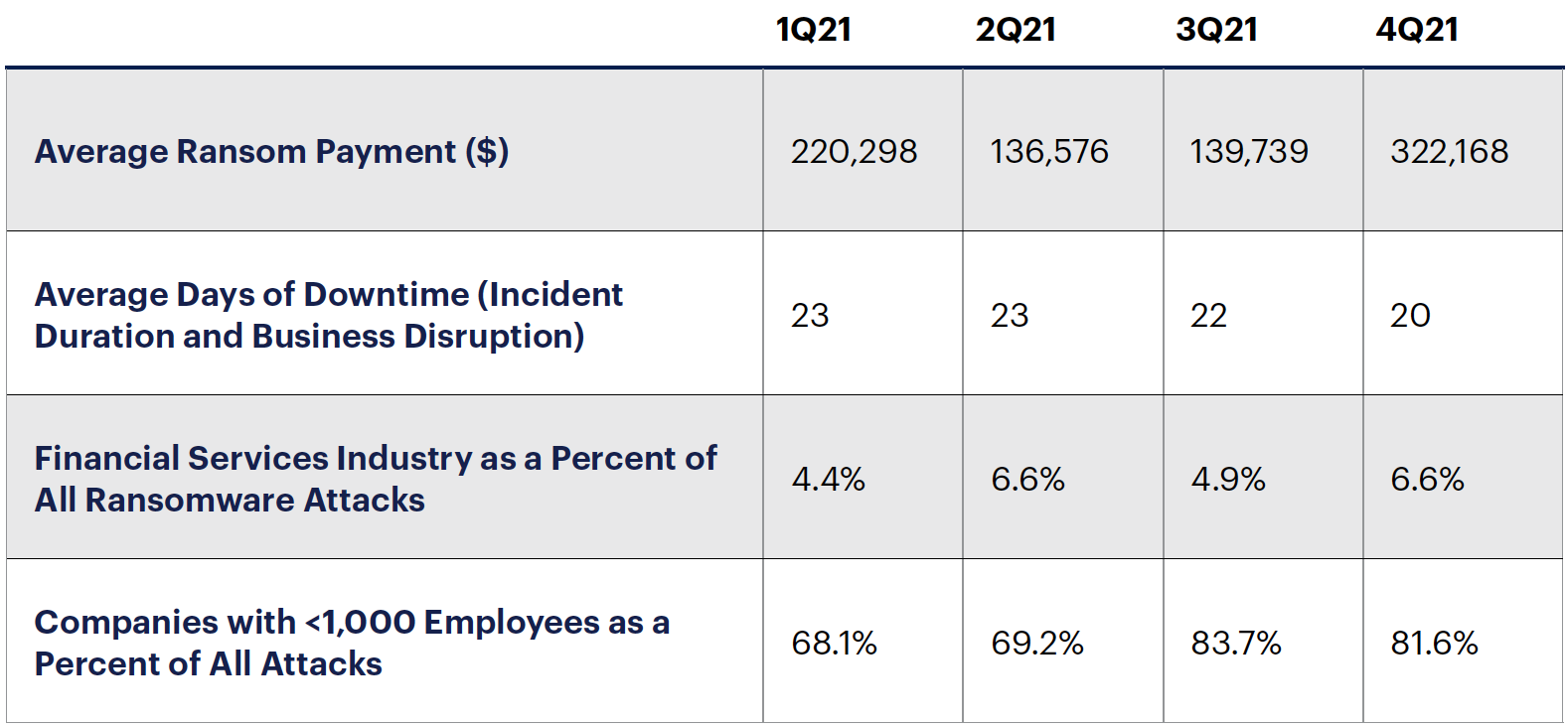
The Table shows the financial losses and operation disruption durations experienced by customers of Coveware, a ransomware mitigation company, because of ransomware attacks.
Table: Ransomware Trends
Sources: Coveware.com: “Ransomware Attack Vectors Shift as New Software Vulnerability Exploits Abound,” April 29, 2021, available at www.coveware.com/blog/ransomware-attack-vectors-shift-as-new-software-vulnerability-exploits-abound; “Q2 Ransom Payment Amounts Decline as Ransomware Becomes a National Security Priority,” July 23, 2021, available at www.coveware.com/blog/2021/7/23/q2-ransom-payment-amounts-decline-as-ransomware-becomes-a-national-security-priority; “Ransomware Attackers Down Shift to ‘Mid-Game’ Hunting in Q3 2021,” October 21, 2021, available at www.coveware.com/blog/2021/10/20/ransomware-attacks-continue-as-pressure-mounts; and “Law Enforcement Pressure Forces Ransomware Groups to Refine Tactics in Q4 2021,” available at www.coveware.com/blog/2022/2/2/law-enforcement-pressure-forces-ransomware-groups-to-refine-tactics-in-q4-2021
Incident Reporting
Given the potential impact that cyber incidents, including ransomware, may have on the financial sector, the federal banking agencies approved a final rule6 to improve the reporting and sharing of information. The final rule, which became effective May 1, 2022, requires a banking organization to notify its federal regulator of any significant computer-security incident within 36 hours. Community banks should review the final rule and take the necessary steps to comply with the requirements in the regulation.
Additionally, community banks that have an established relationship with or services provided by the Federal Reserve’s Financial Services (e.g., FedWire, FedLine Advantage) should be familiar with the reporting requirements under Operating Circular No. 5.7 Prompt reporting of cyber incidents will help to minimize any disruption of services and maintain the integrity of these systems.
Ransomware Outlook for 2022
Ransomware attackers are increasingly targeting small and medium-size businesses, which includes community banks. For the third quarter of 2021, a security firm specializing in ransomware mitigation reported a 14.5 percent increase in the number of attacks targeting organizations with fewer than 1,000 employees.8 Attackers may be focusing on smaller organizations because they have limited information technology and cybersecurity resources to detect and respond to cyberattacks. Attackers may also be wary of targeting large critical infrastructure institutions following the Colonial Pipeline attack, as the United States and other countries have taken swift law enforcement actions against ransomware groups attacking critical infrastructure institutions.
Resources and Guidance
Cybersecurity and Infrastructure Security Agency
The agency offers resources on its ransomware-focused website, www.cisa.gov/stopransomware, including:
- A response checklist, www.cisa.gov/stopransomware/ransomware-guide
- Prevention best practices, www.cisa.gov/stopransomware/how-can-i-protect-against-ransomware
- A list of bad practices, www.cisa.gov/stopransomware/bad-practices
Federal Bureau of Investigation
The FBI has two relevant sites:
- https://ransomware.ic3.gov/default.aspx, to report ransomware incidents and ransom payments made
- www.fbi.gov/scams-and-safety/common-scams-and-crimes/ransomware, detailing best practices for ransomware prevention
Federal Financial Institutions Examination Council (FFIEC)
The FFIEC’s cybersecurity awareness page, www.ffiec.gov/cybersecurity.htm, includes:
- A cybersecurity assessment tool, www.ffiec.gov/cyberassessmenttool.htm
- A cybersecurity resource guide for financial institutions, www.ffiec.gov/press/pdf/FFIEC%20Cybersecurity%20Resource%20Guide%20for%20Financial%20Institutions.pdf
- A statement on cyberattacks involving extortion, www.ffiec.gov/press/PDF/FFIEC%20Joint%20Statement%20Cyber%20Attacks%20Involving%20Extortion.pdf
Financial Services Information Sharing and Analysis Center
The center is an excellent resource for community banks to raise awareness and understanding of current threats, including indicators of compromise to help firms identify potential attacks on their infrastructure. See its website at www.fsisac.com/.
“Sound Practices to Strengthen Operational Resilience”
This joint paper by the Federal Reserve System, the Office of the Comptroller of the Currency, and the Federal Deposit Insurance Corporation has guidance applicable to community banks. The paper is available at www.federalreserve.gov/newsevents/pressreleases/files/bcreg20201030a1.pdf.
- 1 See Penny Crosman, “‘It’s Very Scary’: Small Banks Quietly Hit by Ransomware Attacks,” American Banker, May 24, 2021, available at www.americanbanker.com/news/its-very-scary-small-banks-quietly-hit-by-ransomware-attacks.
- 2 See “Financial Trend Analysis: Ransomware Trends in Bank Secrecy Act Data Between January 2021 and June 2021,” U.S. Treasury Financial Crimes Enforcement Network report, October 1, 2021, available at www.fincen.gov/sites/default/files/2021-10/Financial%20Trend%20Analysis_Ransomware%20508%20FINAL.pdf.
- 3 See “Attacks Surge in 1H 2021 as Trend Micro Blocks 41 Billion Cyber Threats,” Trend Micro, September 14, 2021, available at https://newsroom.trendmicro.com/2021-09-14-Attacks-Surge-in-1H-2021-as-Trend-Micro-Blocks-41-Billion-Cyber-Threats.
- 4 See Bill Toulas, “Pacific City Bank Discloses Ransomware Attack Claimed by AvosLocker,” Bleeping Computer, October 11, 2021, available at www.bleepingcomputer.com/news/security/pacific-city-bank-discloses-ransomware-attack-claimed-by-avoslocker/.
- 5 See Joe Tidy, “How Hackers Extorted $1.14m from University of California, San Francisco,” BBC.com, June 29, 2020, available at www.bbc.com/news/technology-53214783.
- 6 See “Agencies Approve Final Rule Requiring Computer-Security Incident Notification,” available at www.federalreserve.gov/newsevents/pressreleases/bcreg20211118a.htm.
- 7 “Federal Reserve Banks Operating Circular No. 5” is available at www.frbservices.org/binaries/content/assets/crsocms/resources/rules-regulations/063021-operating-circular-5.pdf.
- 8 See “Ransomware Attackers Down Shift to ‘Mid-Game’ Hunting in Q3 2021,” Coveware.com, October 21, 2021, available at www.coveware.com/blog/2021/10/20/ransomware-attacks-continue-as-pressure-mounts.
